Optimize security and specialized connections on the AWS cloud
Recently, CMC Telecom shared in-depth information about Amazon EC2 Instance Connect (EIC) Endpoint – a service that allows users to securely connect to non-routed virtual subnets without going through Bastion Host, IGW or public IP address.

According to CMC Telecom representative, when businesses deploy digital transformation projects on AWS, ensuring security and safe connection to resources in a virtual private network environment from the Internet is one of the priority issues. top first. Normally, we will have to connect to the Bastion Host with a public IP address via an Internet Gateway (IGW) and from the Bastion Host continue to access resources in the private subnet using SSH or RDP.
Because the process of connecting to a private subnet requires many resources and manual steps, AWS has launched the EIC Endpoint service to help customers access resources in the private subnet without having to go through any central application. which time? In addition, EIC Endpoint also helps businesses optimize security investments, feel secure in promoting creativity, thereby being able to respond quickly to all threats and always be safely protected.
In the article below, CMC Telecom experts provide businesses with information about this service, along with how to set up and use Amazon EC2 Instance Connect (EIC) Endpoint to access resources located in the private subnet (in this article is EC2 Instance).
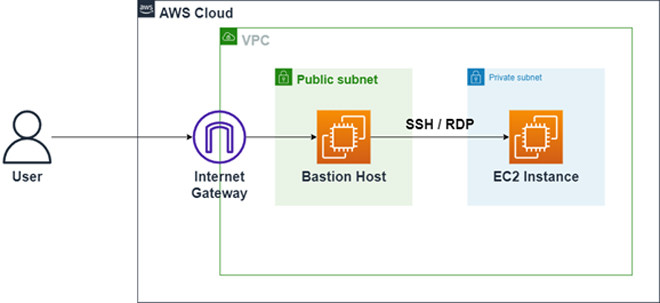
Connect to EC2 instance in private subnet through Bastion Host
Overview of Amazon EIC Endpoint
EIC Endpoint is a service that allows secure access to EC2 instances in a private subnet without the need for an Internet Gateway, Bastion Host or public IP address. EIC Endpoint works with the AWS Console, AWS CLI, and other popular tools like PuTTY and OpenSSH.
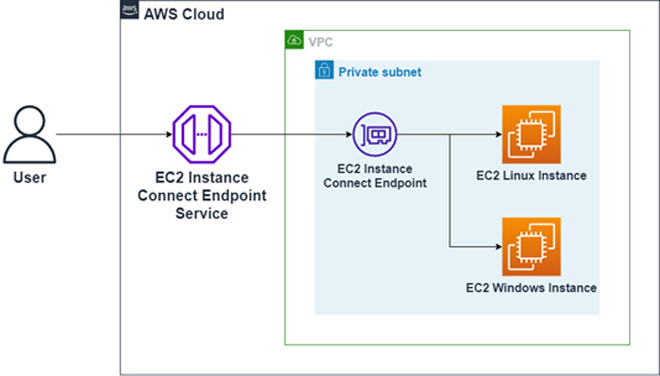
Users connect to EC2 instance in private subnet via EIC Endpoint
According to CMC Telecom experts, EIC Endpoint brings businesses certain benefits when used. First, EIC Endpoint does not require the enterprise VPC to have an Internet connection by using Internet Gateway or NAT Gateway services. Second, businesses do not need to install any additional applications on the EC2 instance when using EIC Endpoint to access. And finally, businesses can use IAM and Security Group to control access.
Enhance security
In addition to the above benefits, EIC Endpoint also helps businesses increase security by combining identity-based authentication and authorization with traditional network controls, providing granular access control, logging, multilayer surveillance and defense.
Specifically, EIC Endpoint controls access based on identity: IAM policies determine who can create and access EIC Endpoint, enforcing authentication and authorization issues. In addition, this service also helps businesses control network standards: Security Groups associated with resources in the VPC are used to allow or deny connection rights. Not only that, EIC Endpoint can separate privileges: the separation between control-plane and data-plane ensures that administrators – users have separate privileges in creating and using endpoints. Finally, there is auditing and logging. The APIs called to the EIC Endpoint are all documented in AWS CloudTrail. This helps businesses see an overview of endpoint activities and check for security issues more effectively.
How to create and use EIC Endpoint to connect to EC2 Instance in Private Subnet
Each VPC has only one EIC Endpoint. To create or modify an endpoint and connect to the EC2 instance, the enterprise must have IAM permissions, and the Security Groups associated with the EC2 instance must have access rights. Businesses can refer to how to configure Security Groups and how to create IAM permissions in the AWS documentation.
After creating the Security Groups and necessary IAM permissions, businesses can follow the following steps to create a connection to the EC2 instance through the EIC Endpoint:
Step 1: Create EIC Endpoint: go to the VPC interface, then select Endpoints and select Create endpoint.
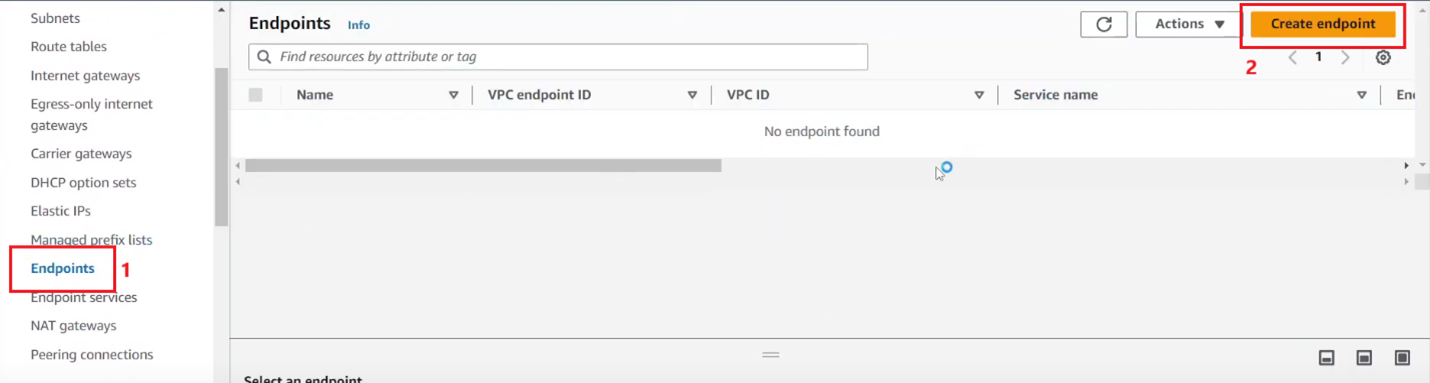
Next, on the Create endpoint page, you need to enter a name for the endpoint in the Name tag section, select EC2 Instance Connect Endpoint.
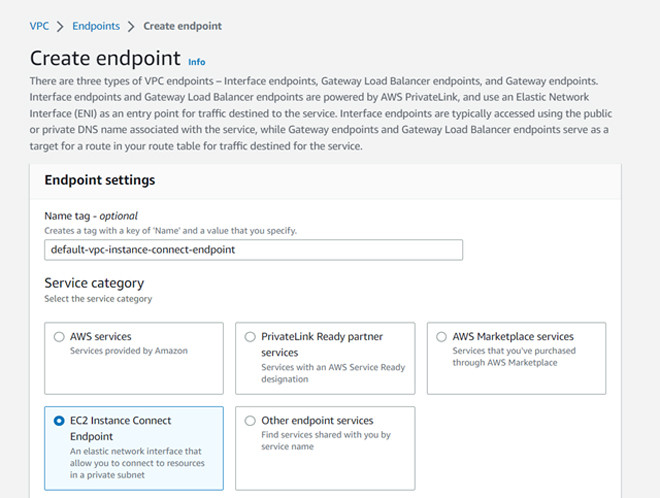
Then select VPC, select previously created Security groups, select Subnet to create EIC Endpoint, then click Create endpoint.
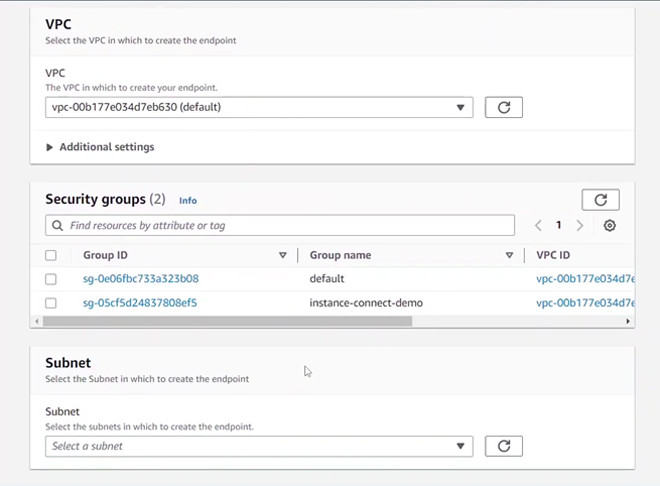
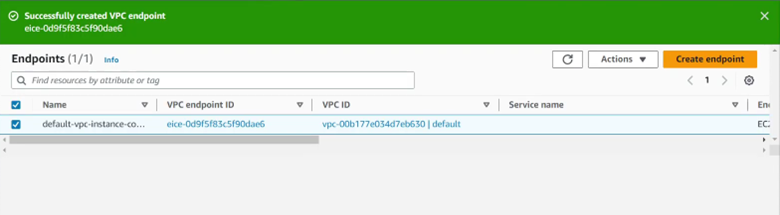
Step 2: Connect to EC2 instance: go to EC2 interface, select Instances, click on the instance you want to connect, select Connect.
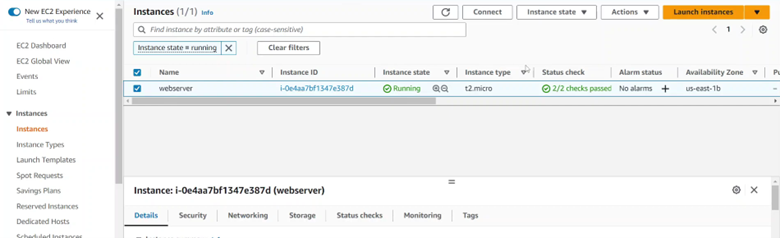
Then, select Connect using EC2 Instance Connect Endpoint, in the EC2 Instance Connect Endpoint section, select the newly created endpoint, then select Connect.
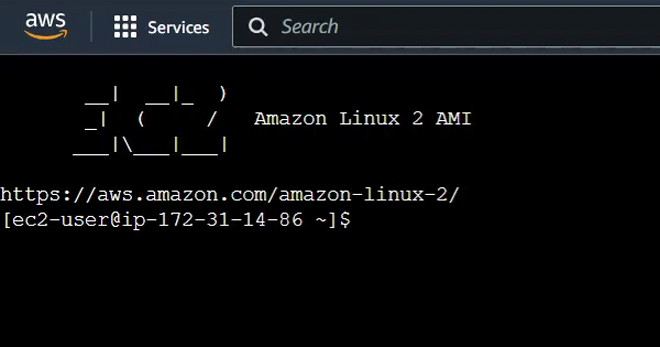
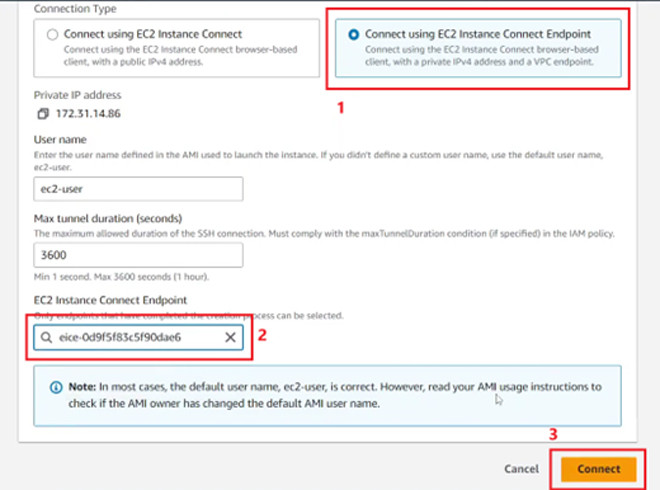 We will then be redirected to the page connecting to the EC2 instance.
We will then be redirected to the page connecting to the EC2 instance.
“We believe that Amazon EC2 Instance Connect Endpoint provides a solution to securely connect to resources and services located in private subnets using SSH or RDP without using Internet Gateway, public IP addresses. and Bastion Host. By configuring an EIC Endpoint for VPC, businesses can securely connect using available tools (PuTTY, OpenSSH, …) or Console/AWS CLI. We hope that the article is useful for businesses,” CMC Telecom representative expressed.
CMC Telecom is currently a advanced partner of AWS in Vietnam. In early 2023, the business received two prestigious awards from the Asian Telecom Awards 2023 for “Innovative Cloud of the Year” and “Innovative Infrastructure of the Year”.










 We will then be redirected to the page connecting to the EC2 instance.
We will then be redirected to the page connecting to the EC2 instance.